< Key Hightlight >
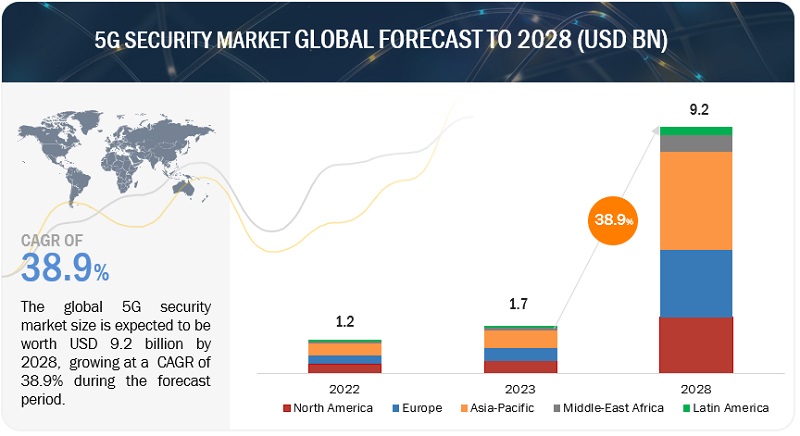
The global 5G security market size is projected to grow from USD 580 million in 2020 to USD 5,226 million by 2026, at a Compound Annual Growth Rate (CAGR) of 44.3% during the forecast period. The 5G security market is gaining traction due to rising security concerns in the 5G networks, increasing ransomware attacks on IoT devices, rising attacks on critical infrastructure, and increasing IoT connections paved way for mMTC with enhanced security requirement.
To know about the assumptions considered for the study, Request for Free Sample Report
COVID-19 impact on the global 5G security market
- The pandemic has decreased the number of greenfield deployments in most regions. Most businesses have postponed their infrastructure-related activities for the upcoming quarters.
- During COVID-19, European telecom operators have announced the availability of a 5G network in several countries.
- As per 5G Observatory data, 5G commercial services have been available in 18 countries by the end of September 2020. These countries include the UK, Sweden, Spain, Slovenia, Romania, Poland, The Netherlands, Latvia, Italy, Ireland, Hungary, Germany, Finland, Denmark, Czech Republic, Bulgaria, Belgium, and Austria
- Ericsson quickly developed four base stations in two days to deliver mission-critical business applications for the healthcare sector over the 5G network in Wuhan, China
- The KSA recorded 344 COVID-19 attacks, including 268 email spam attacks, 59 malware threats detected, and 17 Uniform Resource Locator (URL) attacks. Figures are based on cyber threats that were blocked by Trend Micro
- In July 2020, South Africa's telecoms regulator – Independent Communications Authority of South Africa (ICASA) issued an Invitation to Apply (ITA) for a high-demand spectrum and Wireless Open Access Network (WOAN). This will further accelerate the rollout of 5G services in the country. The ITA will mainly include the following licenses in the range of 700MHz, 800MHz, 2.3GHz, 2.6GHz, and 3.5GHz bands. These bands will be utilized in the 5G network
To know about the assumptions considered for the study, download the pdf brochure
Market Dynamics
Driver: Secutiry concerns in the 5G network
CIOs are largely concerned with a network that can lead to a huge loss for businesses as well as service providers. The new network infrastructure has been designed with the help of SDN, NFV, and cloud-native architecture. Network functions are disaggregated from underline infrastructure and located across local, regional, and central data centers. In a cloud-based 5G network, most network functions are deployed over the public and private cloud infrastructure. The 5G network is connected to vertical industrial networks, such as automobiles, medicine, factories, and IoT devices, as well as the existing legacy networks (2G, 3G, 4G) and internet service networks. It will create a network connection structure that comprises complex heterogeneous networks, centered on the 5G networks. The complexity of these networks can lead to weak linkages arising from the networks and devices with different security requirements and different levels of security technology applied.
Restraints: Delay in the standardization of spectrum allocation
The use of higher frequencies is a major advantage in the development of the 5G network. However, all high frequencies (radio spectrum) are already used for different applications, such as telecommunications services and government agencies. For the development of 5G infrastructure, accessing these high-frequency spectrums is crucial. As it is already allocated for different applications, there is conflict in accessing these frequency bands. However, there is no clarity on the definite timeframe as to when wireless operators would be given access to these spectrums to implement 5G infrastructure. As of now, different regulations are being set by different government agencies across all regions. For instance, Ofcom (UK), UK’s communications regulator, has suggested the allocation of 6 GHz frequency band for 5G infrastructure, while the Federal Communications Commission (FCC) in the US has allocated frequencies from ~24 GHz. In South Korea, the Ministry of Science and ICT auctioned 3.5 GHz and 28 GHz bands for 5G services in June 2018. This irregularity in spectrum allocation and the delay for agreement on spectrum use are the factors hampering the clarity on the exact security requirement, thereby increasing the vulnerability of the network. The standardization of spectrum allocation across regions and countries is extremely important for the development of 5G infrastructure as it impacts the economies of scale, and it also gives clarity to equipment vendors for developing suitable products.
Opportunity: Demand for Private 5G across enterprises, government, and industrial sectors.
Private 5G networks will provide next-generation connectivity for business applications, such as autonomous vehicles, connected factories, connected healthcare, smart retail, and rural broadband connectivity. All these use cases require low latency and higher throughput equips with greater precision. Private 5G networks make use of 5G non-standalone and standalone architecture with the use of licensed and unlicensed bands specifically designed for highly mission-critical business applications. 5G networks will use a network slicing technique that helps enterprises to effectively protect the available resources. North America and Europe region have shown a positive approach toward deploying private 5G networks.
Challenge: Uncertainty around RoI and other unprecedented challenges
5G deployments are in the introductory stage of their product lifecycle with standalone solution-related transitioning that requires significant amount of work. 5G ensures several advantages, such as CUPS and network slicing. Operators need end-to-end 5G networks to be expansible, high-performance, and flexible so that they can efficiently deliver extensive services expected by users, which finally brings competitive advantages to operators. However, the challenges with 5G rollouts, which telcos face include alignment with the company’s long-term interest in the industry being entered and value proposition credibility with respect to the target market segment. The level of market success also depends on the financial investment committed. However, telcos do not want to indulge in over-investments before experiencing RoI or real traction.
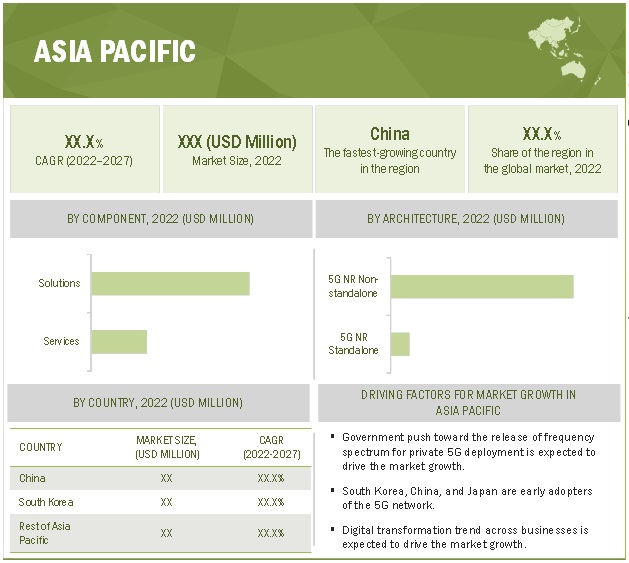
APAC to grow at the highest CAGR during the forecast period
South Korea, China, Australia, and Japan are the prime APAC countries that have started several 5G-related activities; which would provide growth opportunities for 5G security vendors in the region. Asian telecom service providers, vendors, and government firms are determined to take the lead in 5G R&D. Various countries in Asia have either initialized the implementation of smart city projects or are in the planning phase. China is the biggest marketplace in APAC for the development of smart cities. Delivering new video services through enhanced broadband was cited as the most important use case in APAC. Key drivers in Japan and South Korea are connected vehicles and IIoT, while connected healthcare is the most important driver in India, Australia, and Vietnam. 5G network plays an integral role in advanced technologies, such as IoT and Machine-to-Machine (M2M) communication, and sectors, such as smart cities and industrial automation.
Key Market Players
This research study outlines the market potential, market dynamics, and major vendors operating in the 5G security market. Key and innovative vendors in the 5G security market include A10 Networks (US), Akamai (US), Allot (Israel), AT&T (US), Avast (Czech Republic), Check Point (US), Cisco (US), Clavister (Sweden), Colt Technology (UK), Ericsson (Sweden), F5 Networks (US), ForgeRock (US), Fortinet (US), G+D Mobile Security (Germany), Huawei (China), Juniper Networks (US), Mobileum (US), Nokia (Finland), Palo Alto Networks (US), Positive Technologies (UK), Radware (Israel), Riscure (The Netherlands), Spirent (US), Trend Micro (Japan), and ZTE (China). The study includes an in-depth competitive analysis of these key players in the 5G security market with their company profiles, recent developments, and key market strategies.
Scope of Report
Report Metric | Details |
Market size available for years | 2020-2026 |
Base year considered | NA |
Forecast period | 2020-2026 |
Forecast units | Value (USD Million) |
Segments covered | Component (solutions and services), network component security, architecture, end user, deployment type, and vertical |
Regions covered | North America, Europe, APAC, and RoW |
Companies covered | A10 Networks (US), Akamai (US), Allot (Israel), AT&T (US), Avast (Czech Republic), Check Point (US), Cisco (US), Clavister (Sweden), Colt Technology (UK), Ericsson (Sweden), F5 Networks (US), ForgeRock (US), Fortinet (US), G+D Mobile Security (Germany), Huawei (China), Juniper Networks (US), Mobileum (US), Nokia (Finland), Palo Alto Networks (US), Positive Technologies (UK), Radware (Israel), Riscure (The Netherlands), Spirent (US), Trend Micro (Japan), and ZTE (China). |
This research report categorizes the 5G security market to forecast revenue and analyze trends in each of the following submarkets:
Based on Components
- Solutions
- Next-Generation Firewall
- Data Loss Prevention
- Antivirus/Antimalware
- DDoS Protection
- Security Gateway
- Sandboxing
- Others (network access control [NAC] and network vulnerability assessment and penetration testing [VAPT])
- Services
- Consulting
- Implementation
- Support and Maintenance
Based on Network Component Security
- RAN Security
- Core Security
Based on Architecture
- 5G NR Non-standalone
- 5G NR Standalone
Based on End user:
- Telecom operators
- Enterprises
Based on Deployment Type:
Based on Vertical:
- Manufacturing
- Healthcare
- Energy and Utilities
- Retail
- Automotive and Transportation
- Public Safety
- Media and Entertainment
- Others (BFSI, agriculture, and education)
Based on regions:
- North America
- Europe
- APAC
- RoW
Recent Developments:
- In October 2020, Juniper Networks partnered with Telefónica Spain, a leading global service provider, to secure the mobile backhaul of its growing 5G network. Juniper Networks offered Telefónica Spain the Juniper Security Gateway to deliver future-proof, carrier-class security for the provider’s mobile backhaul network.
- In February 2020, A10 networks introduced vThunder TPS – highest-performance virtual DDoS Defense Solution to protect 5G and cloud infrastructures. vThunder TPS provides operators a cost-efficient way to protect their networks and infrastructures without over-provisioning DDoS defense capacity.
- In July 2019, Spirent announced the preview of the new 5G network security and expanded capabilities in its CyberFlood Data Breach Assessment solution in the US. CyberFlood is a powerful, automated solution that generates realistic application traffic and security threats within live or production networks, providing organizations with a continual security assessment of their enterprise network infrastructures.
- In June 2019, Nokia announced the launch of the enhanced security program and established an advanced security testing and verification laboratory: both designed to address the critical security needs of 5G End-To-End (E2E) networks. The company launched DFSEC 2.0 – an enhanced security program to address the critical security needs of 5G wide area networks. Also, Nokia opened "Future X Security" Laboratory (FXSec) – a new security end-to-end testing and verification lab at Nokia Bell Labs, headquarters in Murray Hill, New Jersey (US).
- In September 2019, Palo Alto Networks acquired Zingbox, an IoT cybersecurity corporation. With this acquisition, Palo Alto Networks leverages Zingbox’s IoT security capabilities to provide subscriptions of its NGFW and Cortex platforms to help users secure their connected devices.
Key Benefits of Buying the Report
The report would provide the market leaders/new entrants in this market with information on the closest approximations of the revenue numbers for the overall 5G security market and its subsegments. It would help stakeholders understand the competitive landscape and gain more insights better to position their business and plan suitable go-to-market strategies. It also helps stakeholders understand the pulse of the market and provides them with information on key market drivers, restraints, challenges, and opportunities.





